Know Everything About Network Access Control
In 2020 because of this global pandemic situation, we all know that the future can badly impact us at any time. As businesses adapted to new normal on the backs of natural disasters, global health emergency, and political uncertainty, the network and the digital transformation of doing business moved from a means of thriving to one of sheer survival.
As IT speeded up the digital transformation, we were all pushed through the gap and the adoption curve with many technologies for the future and business practises.
One of the solutions widely used to protect your corporate networks from threats within the network is Network Access Control (NAC). In most NAC solutions, users and devices that try to gain access to on-site resources are subject to safety policies. Digital transformation has broken network perimeters and changed the way users’ function, creating many challenges for organisations, seeking to facilitate access and secure their valuable assets on-site and on-the-cloud.
Challenges in a Hybrid IT environment
- Lack of an integrated solution that spans enterprise access.
85% of organisations are currently in hybrid cloud, because it offers flexible access to a variety of on-site and public/private cloud applications. Even when traditional solutions for Network Access Control protect network users and resources, they do not extend this protection to users who are outside the network or who are using cloud resources. For example, monitoring device compliance and user security policies often lack parity between local, remote and cloud access. This could lead to security loopholes which lead organisations to buy a variety of products to meet different security needs throughout the organisation, increase the spread of the device over the network and increase ownership costs as well as management complexity, with no visibility.
- Lack of well-defined policies for internal users and devices
The 2018 Ponemon report shows that, while most users need not be privileged, even after moving to a different position or organisation, they continue to have access to them. Most of these deficiencies go undetected by user authentication only and no device authentication. A user who logs in via another user's credentials from his device may not be noticed. A Next-Gen NAC solution can ensure that such critical security breaks are closed with well-defined policies.The Ponemon Survey results indicate that organizations in general have loose security policies for access.
Below responses were given as the primary reason for having privileged access rights:
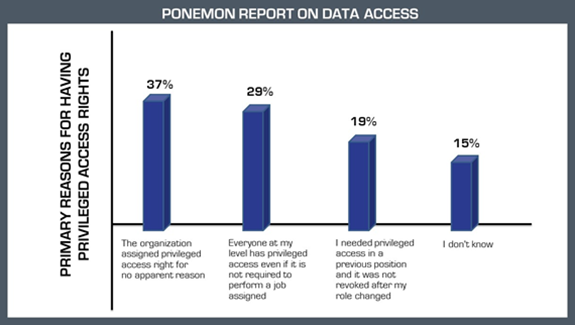
Fig 1. Ponemon report on data access governance
- Increasing legal regulations and focus on compliance.
Regulations such as GDPR are more likely than ever to put pressure on companies to secure user data. A security violation or a loose data governance policy may have a serious effect on the reputation and income of the company. This threat is eliminated because access to data is limited only to those who have authorisation, and that access is implemented across hybrid IT. Next-gen Network Access Control solutions.
- Lack of visibility
If organisations cannot see what type of devices are connected with their network and how they operate, they risk data volatility without knowing that an invisible enemy is harder than a visible one. Currently, most NAC solutions do not provide a single glass panel visibility for all terminals connected to their network, wireless and remote, which allows customers to patch visibility from several sources.
- Threats from BYOD and the Internet of Things (IoT)
The BYOD access is growing as employees feel at home, increases productivity and reduces the operating costs. Bring your own device to work is increasing. Personal devices, however, are susceptible to malware infection by malicious applications which steal or stolen or lost data without any user information, jeopardising sensitive business data. Increasing numbers of IoT devices are connected to the Internet, from webcams and printers to heart rate monitors and medical devices. By 2020, Gartner forecasts that 26 billion IoT devices will be outdated and insecure for most of their firmware, making them vulnerable to cyber-attacks of five-generation like the attack by Mirai Botnet.
- Sponsored-based Guest and Contractor user access challenges.
The first question a company visitor might ask is "Can I access your Wi-Fi for internet?" There may also be many contractor companies that require limited time access to your organisation. Although many solutions for Network Access Control provide solutions for guest access management, they do not have advanced capabilities, such as sponsored, automated on-boarding and timely access. These features can secure guest access and enhance guest experience.
Solution: Remote, cloud and local access unification can help remove traditional and emerging security threats - and provide an excellent user experience.
The unified network access control solution ensures that every user/device attempting to access resources in a business network can be rigorously authenticated through strict policy and monitoring policies, regardless of whether the user is a local, remote or guest user, or regardless of their device – corporate, BYOD or IoT. A Next-Gen Network Access Control solution lets you view all devices on your network and their source in the network as well as ensuring automated response to threats by means of behavioural analysis and security infrastructure integration. If behavioural analysis is suspicious, the solution can activate and take control of adaptive authentication. This solution also enables device or users to be intelligently identified and adapted to the changing platform without needing to log in twice, thereby improving user experience with Single Sign On on site and cloud.
Visibility
You need to know which endpoints are connected, managed and unmanaged to protect and control network access. Network profiling enables the discovery and classification of endpoints and tracks access to the wired and wireless networks between corporate and guest users. Visibility provides a wide range of background information including the role, device type, device configuration, location, time, date, application or network resource and network activity.
Onboarding
Automatic onboarding enables BYOD and IoT device self-registration. The correct level of access to corporate resources is permitted or denied by the security policy. NAC performs a device risk analysis and quarantine suspicious equipment as part of the onboarding process. Self-supply frees IT from onboard work and helps BYOD and IoT deployments to scale.
Security Automation and Orchestration
There is a growing risk of violations being unknown for prolonged periods. Safety incidents can be lost and overlooked in the daily flood of notices without automation. NAC contextual information expands the efficiency of end-point intelligence together with third party security, vulnerability, risk assessment, and system management solutions and provides rapid, automated threat response.

All connections are treated in the same by Zero Trust NAC policies, be it be remote or local. Bidirectional integration of Pulse Policy Secure NAC with the security and access infrastructure allows immediate response to threats at the endpoint level.
Implementation:
A NAC platform needs careful planning and consideration. NAC solutions offer complete view of endpoints and enforce safety policies. There are several considerations about how to use the features available to best meet the needs of your company.
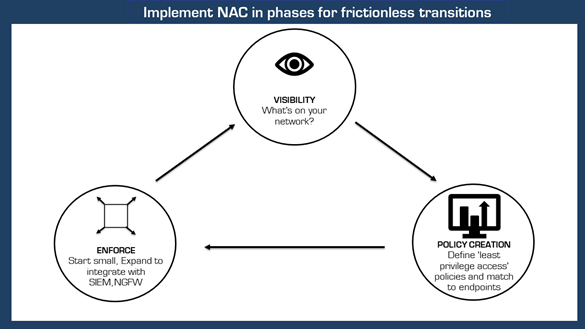
Phases
IT teams use NAC to solve a wide range of access problems for the corporate network. IT organisations see endpoint visibility to managed, unmanaged and IoT devices as table stakes for NAC strategies with a large array of IP and Wi-Fi technologies able to connect to the network.
Furthermore, the NAC addresses workforce change, provides guest access to contractors and partners and enables employee BYOD. NAC technology enables guests and contractors to automate network management while reducing unlicensed users' risks and compromise devices.
With a comprehensive and dynamic network devices perspective, companies can phase in granular policy compliance, ensuring compliance with industry regulations and corporate policy, to secure devices (managed and unmanaged, including IoT devices) and network users. At this stage, companies can leverage existing investments in security infrastructure for an enhanced identity and device context and automated incident mitigation.
Visibility
Consider using NAC visibility characteristics to profile the endpoint continuously with or without an agent, profiling may be carried out. DHCP, SNMP, NMAP, WMI, SSH, EMM and HTTP session details can be used for a variety of polling methods. Additionally, profilers can classify devices, assign profile to endpoints with static IP-addresses, and scan open ports for MAC spoofing actively.
Enforcement
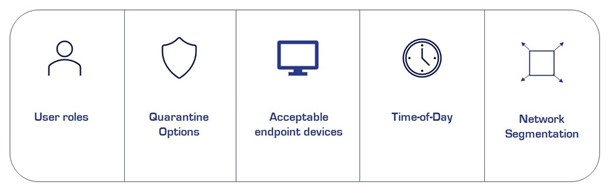
Use NAC database for granular policy implementation for securing devices (managed, unmanaged and including IoT devices) after full visibility. Usin NAC for the implementation of granular policies will ensures that industry regulations and corporate policies are complied with. To achieve an improved identity and device context, or to enable automated mitigation, customers may leverage existing investment in security infrastructure. A wide range of integrated and expensive policy templates are available in NAC solutions. For building policies, categories to consider include:
Integrations
Consider NAC integration through APIs, Syslog and IF-MAP protocol with security solutions from third parties. Implement an Alert-based or API-based NAC solution to share identity, network and configuration contextual information through popular firewalls, SIEM, Enterprise Mobility Management (EMM) and other systems.
802.1X for True Zero Trust
802.1X is a specialised, widely supported dynamic network access control technology on network edge devices such as switches and LAN wireless controllers. It is considered to be a challenge while implementing. A phased deployment, however, ensures that the migration is smooth. It is very easy to maintain once implemented, a lasting payoff that releases IT and the resources of the security team. 802.1X technology is true to the 'validate before connection' principle of Zero Trust and contains direct and ongoing communication with authentication servers. It tracks all endpoints on a port in order to avoid "piggybacking" of additional unassembled devices via a switch or Wi-Fi router on the established validated connection on endpoint.
SNMP or CLI access are alternative control technology for edge network devices (over SSH). MAC authentication combined with a granular visibility and a profiling solution ensures the secure connectivity of headless devices such as printers, IP phones, cameras, etc.
Agent or Agentless
The security compliance on an endpoint may include many variables including AV definitions, operating systems, or other software updates, active apps, etc. This can be evaluated in different ways. Installing an end-point agent is the most secure, granular and responsive option. The agent can provide 802.1X, but this can work with native supplicant of today's operating systems. Agents from vendors such as Pulse Secure that provide additional secure access products such as VPN or SDP, the agent can serve all solutions.




















