Mobile and Wireless Security Explained
Mobile devices are very subjective tools, mainly used to facilitate routine operations, but they also serve to store very confidential personal knowledge and data. Mobile security is the safety and protection of smartphones, tablets, laptops and other portable devices, and the systems they connect to, from threats and vulnerabilities linked with wireless computing.
As we count on heavily on our mobile gadgets, thus growing the value of information and incentive for cybercriminals in addition to the mobile security risks we generally come across one must be watchful for new risks focused on the subsequent 3 key influence parts:
SMiShing: SMiShing attack is initiated via text messages as an alternative of email.
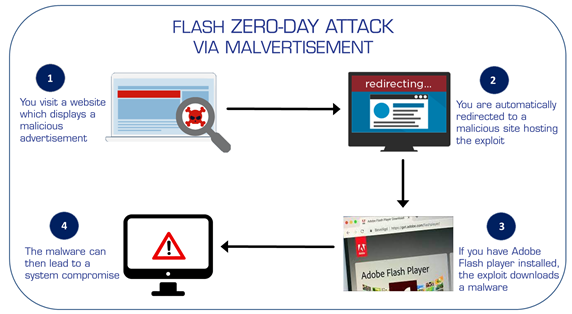
BYOD: As enterprise users are permitted advanced admittance/access from individual mobiles gadgets like smartphones and tablets are efficiently substituting desktops for numerous business duties.
The Internet of Things (IoT): With the numerous kinds of smart devices, they cannot constantly be supervised by customers or antivirus software’s. This makes IoT systems an attractive objective for invaders who make use of them as entry points to the bigger network.

Along with aforementioned attacks we see countless attacks that can occur through wireless security and additionally take the lead to data violation let us try and identify them
- Attacks based on GSM networks
Once the encryption algorithm of GSM is cracked, the invader can capture all unencrypted messages made by the target's/user’s smartphone system.
- Attacks based on lack of Wi-Fi security
An invader can attempt to snoop on Wi-Fi communications to obtain intelligence (e.g username, password).
- Attacks based on Bluetooth
A mobile phone must be in the reach and Bluetooth in discovery mode. The invader sends a file/script via Bluetooth. If the receiver acknowledges the request, a virus is broadcast.
Example: Cabir is a worm that circulates via Bluetooth link/connection.
- Attacks based on Operating system
Occasionally it is feasible to conquer the security defenses by altering the OS itself.
-
Jail-breaking and Rooting
Mobile system consumers take management of their mobile security by jail-breaking it, and modify the interface by launching applications, modify system settings that are not permitted on the gadget.
-
Password Cracking
Strangers may play over-the-shoulder on targets, such as examining particular keystrokes or pattern motions, to unlock gadget password.
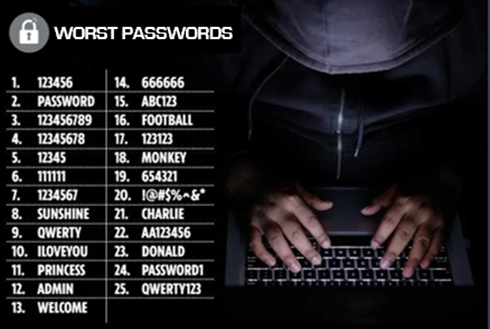
Majority of the outbreaks/attacks we read about have a breakthrough in to our systems through wireless network hence it is very imperative that we also Learn about wireless networks security and wireless protocols used in order to maintain our network wireless security and to abate the data breach and preserve our network.
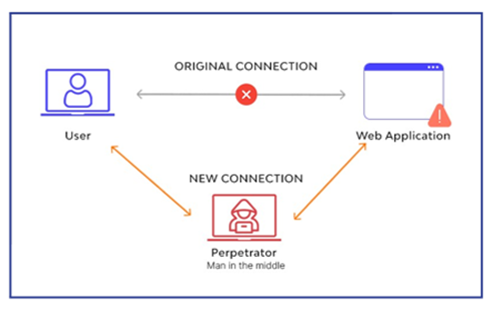
More so, wireless security, also known as Wi-Fi security, intends to safeguard your data and make sure it remains only available to users you give permission to.
WEP- wired equivalent privacy, WPA - wi-fi protected access, WPA2 - wi-fi protected access 2, WPA3 - wi-fi protected access 3 are the wireless security protocols currently available.
Some prominent additives looked for in the wireless security protocol are:
- Superior security for passwords.
- Customized encryption for individual and public networks.
- Extra security for enterprise networks.
To safeguard our mobile systems owing to mobile and wireless security certain key points the manufacturers need to consider are Prolific OS, Secure OS, Trusted Execution Environment, Secure Element, Security Applications so that we can take care of our data and safeguard it irrespective of data breaches and malware activities that may be carried out in the future.
Security is a constant arms race amongst invaders and defenders. Since the mobile system application marketplace is developing at constant time, mobile security will persist to bring surplus issues to cope with.
In other verses, mobile and wireless security is often a topic of evaluating risk and reward, defense versus convenience. The outcome of this article is a general picture of this phenomenon, which investigates the harmful events, circumstances and environments that have the possibility to base the damage of assets, and the security measures that intends to eradicate them and deliver real and suitable shield for a user.




















